Thousands -- possibly hundreds of thousands -- of Twitter users have been hit by a security bug that causes potentially dangerous content to appear on computer screens without warning, according to a researcher at the security firm Sophos.
When users of the popular site "mouse over" a link on Twitter.com, the content appears even if the person did not click on it, says Graham Cluley, the researcher, who recommends users avoid Twitter.com until the issue is fixed.
"It's obviously the most natural thing in the world just to move the mouse across the screen," he said in an interview with CNN. "You don't have to click on a link."
The bad links may also be retweeted, or sent to that person's followers, which causes the security flaw to spread across the network.
The bug could be harmless, doing nothing other than taking users to websites that they did not intend to open, Cluley said. But it also could be exploited by hackers who could use the bug to install malicious software on a person's computer, allowing them to collect personal and financial information, he said.
It appears to affect both the new and old versions of Twitter.com, he said. The site recently updated its look and functionality to include links and videos that open within the pages of Twitter's website. Using the site through third-party software, like TweetDeck or Seesmic, should still be safe, he said.
Twitter on Tuesday morning said it had fixed the security flaw.
"The exploit is fully patched," said Twitter in an update posted at 9:50 a.m. ET on its status blog.
That followed an earlier message from Twitter that said, "We've identified and are patching a XSS attack; as always, please message @safety if you have info regarding such an exploit. We expect the patch to be fully rolled out shortly and will update again when it is."
Several prominent Twitter users appeared to be affected.
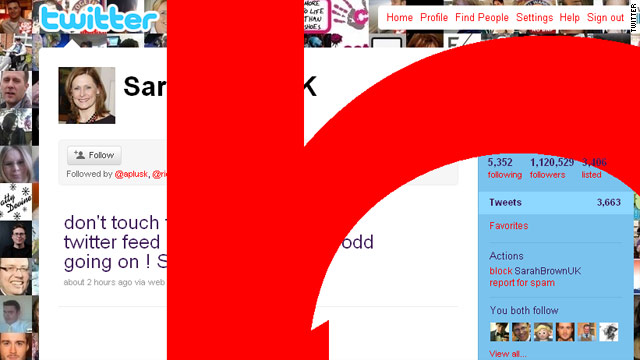
Writing on this blog, Cluley says that Sarah Brown, wife of the former British Prime Minister Gordon Brown, was among those affected by the security hole.
"It appears that in Sarah Brown's case her Twitter page has been messed with in an attempt to redirect visitors to a hardcore porn site based in Japan. That's obviously bad news for her followers -- over one million of them," Cluley writes.
Brown posted this follow-up tweet on Tuesday morning:
"don't touch the earlier tweet - this twitter feed has something very odd going on ! Sarah."
White House press secretary Robert Gibbs also tweeted about the situation:
"My Twitter went haywire - absolutely no clue why it sent that message or even what it is...paging the tech guys..." Gibbs wrote on his Twitter feed.
A video posted by Sophos on YouTube shows the bug in action. When the user's mouse hovers over a problematic tweet, he or she automatically is redirected to another website, which could contain malicious or inappropriate material. The user does not have to click the link to activate the bug.
"It looks like many users are currently using the flaw for fun and games, but there is obviously the potential for cybercriminals to redirect users to third-party websites containing malicious code, or for spam advertising pop-ups to be displayed," Cluley writes on his blog.
It's unclear exactly how the problem started, Cluley said, but a vulnerability in Twitter's code likely has allowed people to stir up the trouble. That flaw may have existed for years, and simply was undiscovered, or it could be new, he said.
"We have seen this kind of thing before -- we've seen worms spreading in a similar way on Twitter before, but it's certainly the largest in recent times," he said.
Users who have been affected should log out of their accounts, disable Java Script and avoid the Twitter.com website until the matter is resolved, Mikko Hypponen, a researcher at the security firm F-Secure, writes on his blog.
"While Twitter's security team is scrambling to close this loophole, we expect problems to continue," Hypponen says.
"It's perfectly possible that there will be more malicious attacks, possibly combining this technique with browser exploits."

